The difference between authentication and authorization
Learn the key differences between authentication and authorization in securing applications. Learn how these processes work together to protect sensitive data and improve cybersecurity with practical examples and best practices.
On the way to secure applications - authentication and authorization
Processes such as authentication and authorization play a key role in the security of applications. Both electronic processes are essential to guarantee that only legitimate users can access sensitive data records and programs.
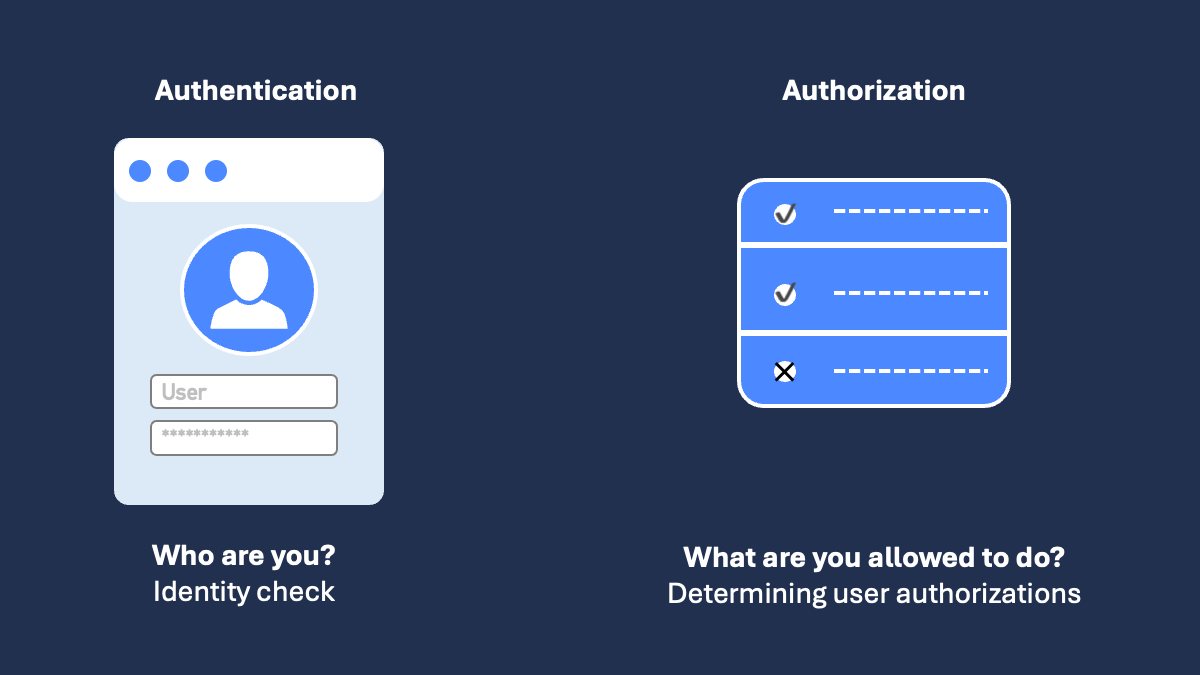
The interaction of authentication and authorization
Every authentication process starts by verifying the identity of a user. This is done using various methods such as password entries or digital checks of biometric data.
Once the user identity has been legitimized, the second security stage is authorization. Here, the user system determines what type of resources and information the previously authenticated user is allowed to access.
By linking the two processes in sequence, a high level of security is achieved. This is because, in addition to checking the user's identity, the corresponding app also defines the relevant access rights.
Staged phases such as two-factor authentication in conjunction with the assignment of usage rights are becoming all the more important as cybercrime increases.
A magnifying glass on the basics of authentication
Authentication is an indispensable standard within IT security.
Implementing this standard ensures that the identity of a user or third-party system is fundamentally checked. More importantly, security precautions are taken in advance, before resource access is possible within the scope of the respective application.
Here are some well-known practical examples that provide an understandable picture of different authentication approaches:
Conventional password-based authentication
When logging in to email accounts or banking apps, users enter their email address and a personal password. However, this method is susceptible to phishing attacks and brute force attacks.
Two-factor authentication (2FA)
For online banking, for example, in addition to the individual password, an additional code must be entered into the control screen as a system-generated one-time password (OTP). The specific OTP is often sent by SMS or e-mail.
Alternatively, a special authentication app such as Google Authenticator is used.
Both levels significantly improve system security. This is because any attacker must know two different key factors before gaining access to the application program.
The tokenized authentication method
This access method is widely used for internal company networks (intranets). Employees use physical security tokens or smartcards in conjunction with a special PIN code to access the program environment.
Such access methods are often used for complex apps in the context of security-critical operating systems.
The biometric authentication approach
The use of infallible fingerprint identification or sensitive facial recognition software is increasingly being discovered on smartphones.
Digital devices such as the Apple iPhone, for example, use highly specific touch IDs or face IDs to verify user identity. Such a verification method is considered extremely secure, as biometric identifiers are unique and difficult to forge.
Single Sign-On (SSO)
Practical SSOs can be used for company and private program packages such as Microsoft Office 365. Each user authenticates themselves once and is then granted access to multiple apps and services.
There is no need to log in again with this security solution. This improves user-friendliness and significantly reduces the number of login credentials required.
Best practices for secure authentication
There are proven principles that enable secure authentication processes.
Password management
- Use complex passwords with a combination of upper and lower case letters, numbers and special characters.
- Change passwords at regular intervals and avoid reusing outdated passwords.
- Use a password manager. This helps to create strong and unique passwords for each system.
Two-factor authentication (2FA)
Use 2FA methods such as biometric data in the form of fingerprints or facial recognition. Physical security tokens may also be advisable.
Multi-factor authentication (MFA)
Combine more than two authentication methods such as password, biometric data and additional tokens for increased security.
The practical implementation of authentication methods
Options for implementing user credentials are Single Sign-On (SSO), OAuth and OpenID Connect as well as JSON Web Tokens (JWT).
Single Sign-On (SSO)
The SSOs process enables users to log in to multiple applications with a single data record. The advantages are improved efficiency of the login processes and a reduced risk of password leaks. This is complemented by centralized administration of user management.
OAuth and OpenID Connect
OAuth is a special authorization protocol that allows access to defined IT resources. The method allows effective authentication processes without the risk of exposing user data.
OpenID Connect is based on the OAuth method as a foundation and adds further authentication options. This makes it possible to implement well-secured, delegated access management for web applications.
JSON Web Tokens (JWT)
JWT is a compact token format that securely transmits authentication information between two or more parties.
The entire structure can be divided into three components: header, payload and signature.
- The header contains the key information about the token type used and the authentication algorithm used.
- The payload contains the relevant authentication data (claims).
- Last but not least, the signature serves to ensure the integrity and authenticity of the authorization token.
The purpose of authorization
Authorization proves to be a basic process that determines accessible resources and data for an authenticated user. All authorization processes ensure that only authorized users can access highly sensitive information and systems.
The two methods used, "role-based access control (RBAC)" and "attribute-based access control (ABAC)", have different advantages: RBAC is more straightforward to implement and manage, while ABAC guarantees a sophisticated, context-centered access check.
Role-based access control (RBAC)
Role-based access control assigns users specific functions that include clearly defined authorizations. Such role assignments are usually based on selected management positions or other user tasks within a business organization.
For example, a controlling specialist has access to relevant financial data, while an IT administrator has extended system rights. RBAC is efficient in that all authorizations can be centrally managed and easily modified.
Attribute-based access control (ABAC)
Attribute-based access control goes one step further by regulating user access on the basis of attributes.
Such attributes include user characteristics (such as affiliation to a specialist department or management position), resource characteristics (such as data sensitivity) or context information (for example: time of access).
ABAC thus guarantees finely tuned, flexible control options based on the security architecture. This is because all access decisions are based on a large number of precisely adjustable criteria.
The implementation of authorization methods in operational practice
A minimal privilege means that all users are given the least possible access rights, which are essential for the performance of their tasks. This economical authorization standard significantly reduces the risk of misuse and unauthorized access.
System administrators of the security architecture implement this basic standard through periodic reviews of access rights and the use of role-based access controls (RBAC).
Furthermore, dynamic authorization ensures that all access decisions are made in real time with regard to current context details. Typically, these are specific characteristics such as user location, device information or current network conditions.
Commercial enterprises are more frequently using attribute-based access controls (ABAC) to effectively make such dynamic authorization decisions. This approach enables a fine-tuned and context-oriented access check.
In specialized enterprise environments, role-based access control (RBAC) is more commonly used. This enables controlled access to sensitive data and systems to be implemented in the best possible way. System administrators are thus able to manage functional roles at a central level and easily adjust all user rights.
Through a smart combination of the two access principles, companies develop a stable, flexible control strategy that optimally combines security and user-friendliness.
The particular challenges for system security and key solutions
Common security vulnerabilities and cyber attacks through phishing, brute force and session hijacking are significant risk factors for IT systems.
Checks and adjustments to access rights as well as dynamic authorization methods are therefore recommended as measures to improve IT security.
This is because the former approach makes it easier to check that no unnecessary access rights are assigned by mistake. Access decisions on a real-time basis using dynamic authorization methods also offer additional efficiency.
To increase IT security, pragmatic measures such as the use of firewalls and intrusion detection systems (IDS) can be added.
Phishing
Attackers deceive users with fake e-mails or websites. Their primary goal is to steal sensitive data such as passwords or credit card details.
Proven solutions are the installation of anti-phishing software, the targeted use of email filters and training to raise employee awareness.
Brute force
Cyber criminals try to decrypt passwords by systematically trying out all conceivable combinations.
Solutions include the use of complex passwords, the implementation of account lockout algorithms after several failed login attempts and the use of two-factor authentication (2FA).
Session hijacking
Attackers misuse a temporary user session to gain illegal access to software systems.
Suitable countermeasures include the use of secure communication protocols (such as HTTPS) and the regular renewal of session tokens. Automatic detection and interruption of suspicious sessions can also be used.
The importance of authentication and authorization methods for marketing and digitalization
Authentication and authorization processes are crucial for marketing managers and digitalization experts.
Here is a typical practical example:
Authentication process: An existing customer logs into an e-commerce website with their username and password.
Authorization process: The subsequent data assignment to the authorized user determines which resources they are allowed to access.
Using the practical example: After logging in via the authentication process, the regular customer is allowed to view their order history.
The practical example clearly shows that the efficient interaction of a clear authentication process and a seamless subsequent authorization method improves user-friendliness and therefore the customer experience. This is because customers feel secure and treated with trust.
Conclusion
On the way to secure applications, modern authentication and authorization procedures are central components of digital transformation. Forward-looking approaches such as multi-factor authentication and role-based access controls increase the security standards of IT applications.
Efficient implementation of these two access options is therefore groundbreaking when it comes to protecting applications from unauthorized access and data misuse. At the same time, such data protection measures ensure the integrity of IT systems.